#01
We don't replace analysts, we enhance their capabilities
We don’t sell dreams, we don’t sell revolution.
Having participated in the rise of cyber in France, we know only too well that technology is important, but the human element will always be necessary. That’s why we focus on supporting the work of analysts.
Our Goal
Put their knowledge and expertise to work and expertise for the benefit of your organization
-
during the EDR setup
-
during supervision
-
during remediation
#02
We don't prevent breaches, we improve your Resilience
Providing the means to block attacks is an imperative but it’s the bare minimum.
An EDR must give you all the contextual elements linked to security events. Every organization needs to understand what happened, how it happened and what was done to stop the threat.
Only then can your company’s resilience be improved.
Our Differentiator
We’ve chosen to build our solution around widely recognized, open formats. The good news is that you can find these rules categorized in the MITRE ATT&CK matrix. The benefit to you is twofold.
-
Make doubt elimination child's play and reduce analyst fatigue
-
Understand the techniques most commonly used by attackers and guide your team's prioritization efforts.
-
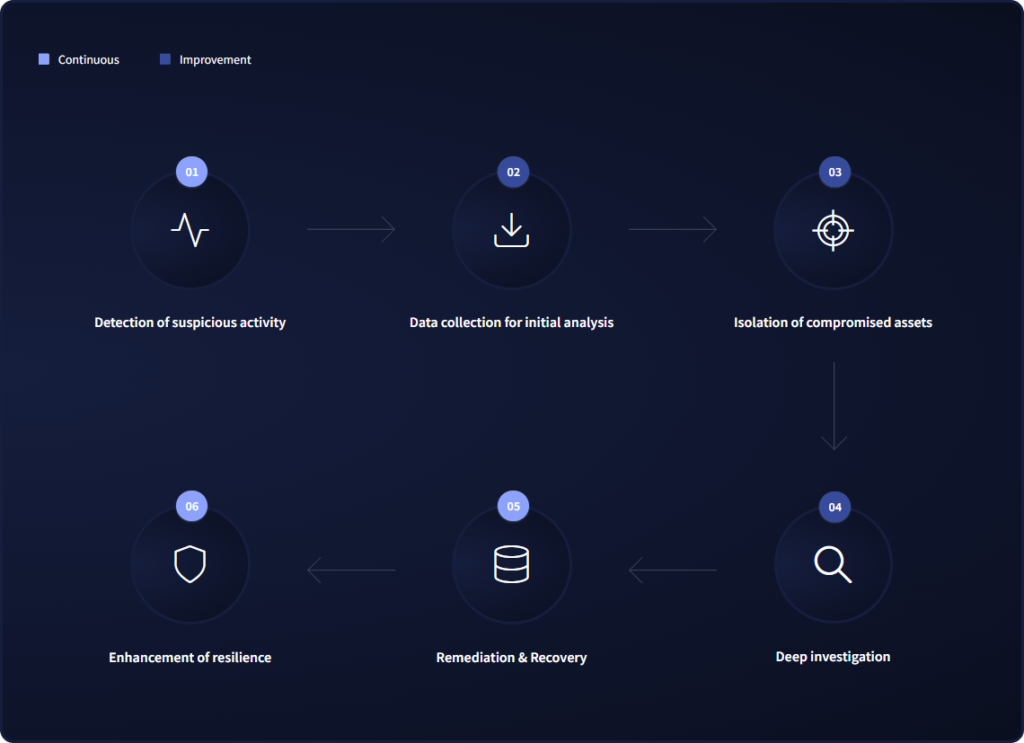
Continuous
-
Improvement
Detection of suspicious activity

01
Data collection for initial analysis

02
Isolation of compromised assets

03
Enhancement of resilience

06
Remediation & Recovery

05
Deep investigation
04
#03
We Don't Provide the Solution, We Enable You to Compose the One You Need
We’re not in the best position to identify your cyber roadmap. You are!
Who else but you has the insight into your organization’s context, its maturity and the means at your disposal to combat cyber risks?
our positioning
-
Help you implement your strategy by offering you the best connectors on the market
-
Enable you to reconcile analyst relevance with independence from suppliers
#04
We don't do AI, we respond to use cases with mathematical models
Let’s face it, AI is a bit of a pie in the sky when it comes to tech solutions. So much so, in fact, that we’re still reluctant to say we’re doing anything about it.
Our aim is not to create AI, but to provide the best possible response to your needs. In short, we focus on identifying use cases and responding to them in the most relevant way. SomSMBmes (and more and more often) this means using mathematical models.
To improve responsiveness, and therefore safety, we have managed to deploy all these models directly in our agents.
Our AI Models
-
Hibou Model
Deep Learning
Predicts the probability of a file being malicious
-
Chocard Model
Machine Learning
Detects malicious PowerShell scripts
-
Condor Model
Machine Learning
Detects malicious executable files
Our Results
-
Shikitega, the “particularly stealthy” malware discovered by AT&T Cybersecurity.
-
Symbiote, the “virtually undetectable threat” discovered by BlackBerry.
And many other types of malware for which no one dares to question their stealth.
#05
We don't protect your endpoints, we maintain your company's production capacity
You’re not just there to protect your organization. Your mission is much broader.
The CISO’s mission is to ensure the continuity of the company. To ensure that the business can continue to operate in the future.
To do this, they need to be able to work properly today. In other words, endpoint security must be achieved without any impact on the business.
Our impact on the business
-
~130 MB RAM
-
0,5% CPU
-
No Device Restart
